nmap -sVC 10.10.10.95 Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-18 06:57 CEST Stats: 0:00:02…

thm – retro
Enumeration
starting with nmap default scan
nmap -sVC -Pn 10.10.108.63
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-05 06:49 CEST
Nmap scan report for 10.10.108.63
Host is up (0.060s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: RETROWEB
| NetBIOS_Domain_Name: RETROWEB
| NetBIOS_Computer_Name: RETROWEB
| DNS_Domain_Name: RetroWeb
| DNS_Computer_Name: RetroWeb
| Product_Version: 10.0.14393
|_ System_Time: 2021-04-05T04:49:36+00:00
| ssl-cert: Subject: commonName=RetroWeb
| Not valid before: 2021-04-04T04:45:54
|_Not valid after: 2021-10-04T04:45:54
|_ssl-date: 2021-04-05T04:49:37+00:00; +7s from scanner time.
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 6s, deviation: 0s, median: 6s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 14.94 seconds
next step after i see port 80/443 dir-scan and sometimes file extension scan
#gobuster dir -u 10.10.108.63 -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.108.63
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2021/04/05 07:00:39 Starting gobuster in directory enumeration mode
===============================================================
/retro (Status: 301) [Size: 149] [--> http://10.10.108.63/retro/]
===============================================================
2021/04/05 07:22:45 Finished
===============================================================
Take a look at the website
after clicking on every link and carefully looking for some hints I find an interesting post:

the user wade is posting a reminder, often these are passwords.. let`s give it a try.
start Remmina and log in with User: Wade, Password: parzival and we are logged in with RDP and got the user flag.
Escalation of Privileges
First thing after login was open the chrome, there was a bookmark for a special CVE and there a some google searches in the History regarding this CVE that can be a hint.

After multiple trys I got an bugW with windows where i can not choose a browser to open the verisign page.
https://github.com/jas502n/CVE-2019-1388
later I try to get another way to get more privileges, get sysinfo and started wesng
https://github.com/bitsadmin/wesng
I decided to give CVE-2017-0213, downloadeed the .exe started webserver on my parrot machine and transferred the file to the windows machine.
https://github.com/WindowsExploits/Exploits/tree/master/CVE-2017-0213
I executed the CVE-2017-0213.exe and cmd as „nt authority\system“ check.
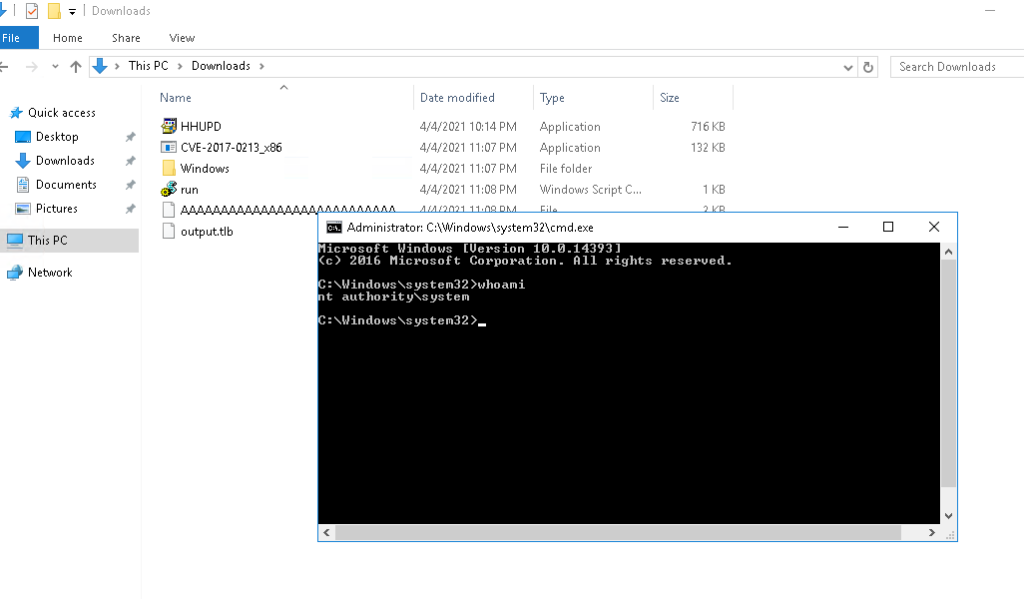
now you can navigate to the admin desktop and get the root flag.